We’d like to remind Forumites to please avoid political debate on the Forum.
This is to keep it a safe and useful space for MoneySaving discussions. Threads that are – or become – political in nature may be removed in line with the Forum’s rules. Thank you for your understanding.
📨 Have you signed up to the Forum's new Email Digest yet? Get a selection of trending threads sent straight to your inbox daily, weekly or monthly!
Has MSE helped you to save or reclaim money this year? Share your 2025 MoneySaving success stories!
PC been hacked how do I protect my bank accounts ?
Comments
-
Downloading an attachment can secretly install malware (a virus) which can do virtually anything imaginable. There are thousands of different malwares which can do whatever you need it to. Hackers can: control your computer, move your mouse and run programs etc, Turn on microphone and camera and record, steal files, log keytrokes to havest usernames/passwords, read and send emails, even access other computers on your home wifi network, access IOT devices on the network such as security cameras, tvs, thermostats etc. Its pretty incredible what is possible.km1500 said:it would be interesting to know how clicking on a link and downloading an attachment and even running an attachment would lock you out of your Steam account and your google account.
does anybody have any idea how this works?
Ex Sg27 (long forgotten log in details)Massive thank you to those on the long since defunct Matched Betting board.2 -
Technically not - this is off topic really, but if a platform is using reasonably up to date encryption techniques (you'd imagine most banks and big platforms are) such as SHA-256 and other techniques such as salting then brute forcing stolen password hashes would take a powerful computer years depending on the complexity of the password, and when ultra complex passwords are used it would likely take a team of computers thousands of years.
Sg28 said:A decent hacker with enough resourses can crack most encryptions.
It's when people use dictionary words or common silly passwords such as secret123 etc on platforms with weaker security measures where password hashes can be brute forced in a blink of an eye.3 -
Yes which Is why I said most. However an individual sitting at home with one pc is probably not likely to keep up to date with the latest encryption methods and would still be vulnerable.booneruk said:
Technically not - this is off topic really, but if a platform is using reasonably up to date encryption techniques (you'd imagine most banks and big platforms are) such as SHA-256 and other techniques such as salting then brute forcing stolen password hashes would take a powerful computer years depending on the complexity of the password, and when ultra complex passwords are used it would likely take a team of computers thousands of years.
Sg28 said:A decent hacker with enough resourses can crack most encryptions.
It's when people use dictionary words or common silly passwords such as secret123 etc on platforms with weaker security measures where password hashes can be brute forced in a blink of an eye.
I think the most common password is still something like 123456. I remember reading something like the top 5000 most common passwords will give you access 20% of all accounts. Pretty crazy.
For people forgetful or none tech savvy a good compromise is a pass phrase rather than a single word. Like Housediamondtelevision for example.Ex Sg27 (long forgotten log in details)Massive thank you to those on the long since defunct Matched Betting board.0 -
dunstonh said:We gave the Yubi keys a go (similar to Titan) but found they just got left plugged into the USB slot, which was fine if there was a remote hack/theft but not pretty useless if it was a physical theft.You can get YubiKeys that also require a fingerprint for authentication:Both YubiKey and Titan support the Fido 2 protocol.2
-
The tools mentioned upthread would be suitable, but the Achilles heel of any encrypted vault is that it must be decrypted to access the contents. As you've pointed out, doing that on a compromised device effectively hands the keys and contents to anyone monitoring.Sg28 said:
Yes which Is why I said most. However an individual sitting at home with one pc is probably not likely to keep up to date with the latest encryption methods and would still be vulnerable.booneruk said:
Technically not - this is off topic really, but if a platform is using reasonably up to date encryption techniques (you'd imagine most banks and big platforms are) such as SHA-256 and other techniques such as salting then brute forcing stolen password hashes would take a powerful computer years depending on the complexity of the password, and when ultra complex passwords are used it would likely take a team of computers thousands of years.
Sg28 said:A decent hacker with enough resourses can crack most encryptions.
It's when people use dictionary words or common silly passwords such as secret123 etc on platforms with weaker security measures where password hashes can be brute forced in a blink of an eye.
I think the most common password is still something like 123456. I remember reading something like the top 5000 most common passwords will give you access 20% of all accounts. Pretty crazy.
For people forgetful or none tech savvy a good compromise is a pass phrase rather than a single word. Like Housediamondtelevision for example.
1 -
And of course, people who use simple passwords could well use them for all their services too. Imagine if they used letmein123 for their PC login, email accounts, bank, social media etc and their PC was compromised. Ouch.Sg28 said:
For people forgetful or none tech savvy a good compromise is a pass phrase rather than a single word. Like Housediamondtelevision for example.1 -
This isnt the case if passwords are strong and changed regularly and re-encrypted with the latest algorithms. Minimum of every year.Sg28 said:
A decent hacker with enough resourses can crack most encryptions.jimexbox said:
An encrypted file is useless to anyone without the key. Be that a hacker or a thief.masonic said:
Such a precaution is useful in case the device is lost or stolen, but not much use if the contents are accessed on a compromised device.jimexbox said:
Hopefully they don't save all passwords/log-in infomation in a file?sparkiemalarkie said:Hi DS PC has been hacked how s the best way to protect his bank accounts?
sxIf anyone does store sentive information on their PC, use something like Veracrypt to strongly encrypt the file. Or better, encrypt the file to a usb stick.
Unlikely they'd bother with the effort for a random individual, unless its poor encryption.0 -
yes thank you for that I understand what you are saying but what I would like to know is how an executable attachment that you download can lock you out of your Steam and Google accounts ie what would it do to accomplish thisSg28 said:
Downloading an attachment can secretly install malware (a virus) which can do virtually anything imaginable. There are thousands of different malwares which can do whatever you need it to. Hackers can: control your computer, move your mouse and run programs etc, Turn on microphone and camera and record, steal files, log keytrokes to havest usernames/passwords, read and send emails, even access other computers on your home wifi network, access IOT devices on the network such as security cameras, tvs, thermostats etc. Its pretty incredible what is possible.km1500 said:it would be interesting to know how clicking on a link and downloading an attachment and even running an attachment would lock you out of your Steam account and your google account.
does anybody have any idea how this works?0 -
Malware could feasibly scan the computer for various accounts, Steam etc and then try at guessing passwords (a password to begin with could have been keylogged, or brute forced from the infected PC).yes thank you for that I understand what you are saying but what I would like to know is how an executable attachment that you download can lock you out of your Steam and Google accounts ie what would it do to accomplish this
Enter a password wrong too many times = account locked. This goes for humans or malware.
Quite often online services have activity pages, it might be worth looking here to see what's listed (I wouldn't log into these on a device that might be compromised by the way)
https://help.steampowered.com/en/accountdata/SteamLoginHistory
https://accounts.google.com/ServiceLogin?service=statement
https://account.live.com/Activity
There'll also be account recovery processes that can be completed for each of these services - again, ensure a non compromised device is used.
I suspect you're not being told the full story - downloading something malicious and running it on a Windows machine should have set off all kinds of warnings from the built in Microsoft Defender. "Untrusted program" etc. If these warnings were ignored then it's anything can happen territory.
The warning would have looked something like this: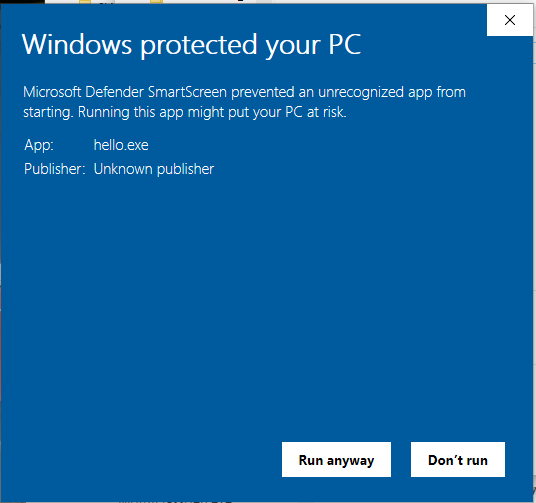
1
Confirm your email address to Create Threads and Reply

Categories
- All Categories
- 352.9K Banking & Borrowing
- 253.9K Reduce Debt & Boost Income
- 454.7K Spending & Discounts
- 246K Work, Benefits & Business
- 602.1K Mortgages, Homes & Bills
- 177.8K Life & Family
- 259.9K Travel & Transport
- 1.5M Hobbies & Leisure
- 16K Discuss & Feedback
- 37.7K Read-Only Boards




